Home
>
Computers & Technology
>
Networking & Cloud Computing
>
Internet, Groupware, & Telecommunications
Internet, Groupware, & Telecommunications
epub |eng | | Author:Ryan Teeter & Karl Barksdale
Using Help and signing out of Google Docs If you don’t understand something (we can’t describe every obscure detail in this book), click the Help link to find out more. ...
( Category:
Enterprise Applications
March 4,2020 )
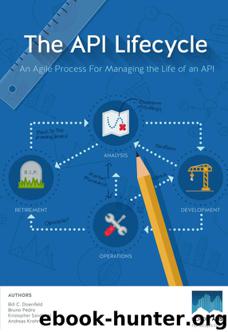
epub |eng | 2015-07-07 | Author:Doerrfeld, Bill & Krohn, Andreas & Sandoval, Kristopher & Pedro, Bruno
5: Use Hypermedia For Evolvability It is impossible to talk about API design without mentioning Hypermedia, a subject that came up in several presentations during the Nordic APIs World Tour ...
( Category:
Agile
March 4,2020 )
epub |eng | 2018-08-06 | Author:Andy Gumbrecht Alex Soto Bueno & Jason Porter [Andy Gumbrecht Alex Soto Bueno and Jason Porter]
6.1.2. Contracts and microservice applications Each microservice has its own lifecycle, is deployed in its own runtime, and lives remotely from other microservices. In this scenario, any change to the ...
( Category:
Software Development
March 3,2020 )
epub |eng | 2017-11-07 | Author:Emilio Rodriguez Martinez [Emilio Rodriguez Martinez]
#import "FrequencyDetector.h" #import "SCListener.h" NSString *freq = @""; @implementation FrequencyDetector RCT_EXPORT_MODULE(); RCT_EXPORT_METHOD(getFrequency:(RCTResponseSenderBlock)callback) { double power = [[SCListener sharedListener] averagePower]; if(power < 0.03) { //ignore low volumes freq = @"0"; } ...
( Category:
Software Development
March 3,2020 )
azw3 |eng | 2017-10-24 | Author:Karl Blanks & Ben Jesson [Blanks, Karl]
the word is indicates that the verb is hiding elsewhere. In this case, it’s in the word improvement. You should rewrite the sentence as follows: I recommend we improve the ...
( Category:
Web Marketing
March 3,2020 )
epub |eng | 2013-07-26 | Author:Bazzell, Michael [Bazzell, Michael]
In January, connect to annualcreditreport.com and request a free report from Equifax. In May, request a free report from Experian. In September, request a free report from TransUnion. These months ...
( Category:
Privacy & Online Safety
March 2,2020 )
epub |eng | 2014-09-08 | Author:Brian S McWilliams [McWilliams, Brian S]
Cowles was hashing out an entirely different set of questions in his cell at the Wood County Justice Center. He was astounded that state attorneys in Florida had decided to ...
( Category:
Email Administration
March 2,2020 )
mobi, epub |eng | 2016-03-18 | Author:Michael Miller
* * * ScreenTips If you’re not sure just what a button on the Ribbon does, you’re not alone—those little graphics are sometimes difficult to decipher. To display the name ...
( Category:
Internet, Groupware, & Telecommunications
March 1,2020 )
mobi |eng | 2015-07-07 | Author:Bill Doerrfeld & Andreas Krohn & Kristopher Sandoval & Bruno Pedro [Doerrfeld, Bill]
5: Use Hypermedia For Evolvability It is impossible to talk about API design without mentioning Hypermedia, a subject that came up in several presentations during the Nordic APIs World Tour ...
( Category:
Agile
March 1,2020 )
azw3 |eng | 2015-08-30 | Author:Karla Mantilla [Mantilla, Karla]
Eleanor O’Hagan, journalist and columnist for the Guardian, concurs: To me, misogynistic abuse is an attempt to silence women. Traditionally, men have been the ones who influence the direction of ...
( Category:
Hacking
March 1,2020 )
azw3, mobi, epub |eng | 2014-11-25 | Author:Timothy Moran [Moran, Timothy]
SammyJS has been added as a dependency and injected in. The RequireJS configuration isn't shown, but it doesn't require a shim. SammyJS plays nicely as an AMD. The pageVm object ...
( Category:
JavaScript Programming
March 1,2020 )
epub |eng | 2015-08-30 | Author:Mantilla, Karla
Eleanor O’Hagan, journalist and columnist for the Guardian, concurs: To me, misogynistic abuse is an attempt to silence women. Traditionally, men have been the ones who influence the direction of ...
( Category:
Hacking
March 1,2020 )
epub, mobi, pdf |eng | | Author:Norman Maurer Marvin Allen Wolfthal
You may find it useful to review the previous chapters on ChannelHandler and codecs, as these will provide the material for our examples. 9.1. Overview of EmbeddedChannel You already know ...
( Category:
Software Development
March 1,2020 )
The InfoSec Handbook: An Introduction to Information Security by Rao Umesh Hodeghatta & Nayak Umesha
epub |eng | 2014-09-01 | Author:Rao, Umesh Hodeghatta & Nayak, Umesha [Rao, Umesh Hodeghatta]
Figure 8-4. Symmetric Key Distribution Center Asymmetric Key Cryptography There are two problems with symmetric key cryptography: Distribution of key – Secret key sharing among senders and receivers. If there ...
( Category:
Internet, Groupware, & Telecommunications
March 1,2020 )
mobi, epub |eng | 1998-09-01 | Author:Claude E Shannon & Warren Weaver
where is the duration of the sth symbol leading from state i to state j and the Bi satisfy then H is maximized and equal to C. By proper assignment ...
( Category:
Number Theory
March 1,2020 )
Categories
Popular ebooks
The Mikado Method by Ola Ellnestam Daniel Brolund(21661)Kotlin in Action by Dmitry Jemerov(18358)
Grails in Action by Glen Smith Peter Ledbrook(16143)
Sass and Compass in Action by Wynn Netherland Nathan Weizenbaum Chris Eppstein Brandon Mathis(13829)
Configuring Windows Server Hybrid Advanced Services Exam Ref AZ-801 by Chris Gill(7510)
Azure Containers Explained by Wesley Haakman & Richard Hooper(7508)
Running Windows Containers on AWS by Marcio Morales(7057)
Microsoft 365 Identity and Services Exam Guide MS-100 by Aaron Guilmette(5444)
Microsoft Cybersecurity Architect Exam Ref SC-100 by Dwayne Natwick(5282)
Combating Crime on the Dark Web by Nearchos Nearchou(5029)
The Ruby Workshop by Akshat Paul Peter Philips Dániel Szabó and Cheyne Wallace(4711)
Management Strategies for the Cloud Revolution: How Cloud Computing Is Transforming Business and Why You Can't Afford to Be Left Behind by Charles Babcock(4558)
Python for Security and Networking - Third Edition by José Manuel Ortega(4284)
The Age of Surveillance Capitalism by Shoshana Zuboff(4264)
Learn Wireshark by Lisa Bock(4183)
Learn Windows PowerShell in a Month of Lunches by Don Jones(4126)
The Ultimate Docker Container Book by Schenker Gabriel N.;(3930)
Ember.js in Action by Joachim Haagen Skeie(3881)
DevSecOps in Practice with VMware Tanzu by Parth Pandit & Robert Hardt(3616)
Windows Ransomware Detection and Protection by Marius Sandbu(3588)